Hello,
I have some questions :
1) Homework 7, "Security With security fixes", question 1.
Is it corrected if A sends K{m}, H{K, m} ? So B will decrypt K{K{m}} = m and then compare by applying H{K, m}. In other words, why do we also encrypt the hash ?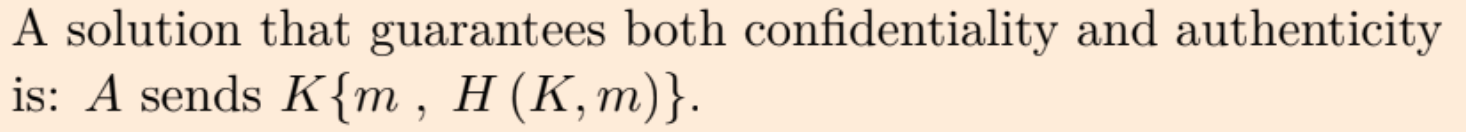
2) Homework 7, "The role of sequence numbers", question 3.
Why the solution is not only to send an integer number that increases at each send. So if a send is delayed or deleted, the receiver could verify with this integer (instead of resending all the previous messages).
So Alice could send : KB+{mi, KA−{H(nB, mi, counter)}}
Moreover, in the solution proposed there is written : "[...] at the end of their communication.". Why do they have to wait until the end of the communication ? Doesn't that imply that they will do the verification too late ?

3) Finally, I just want to make sure that the notations K{x, y} and H(x, y) means a tuple, right ?