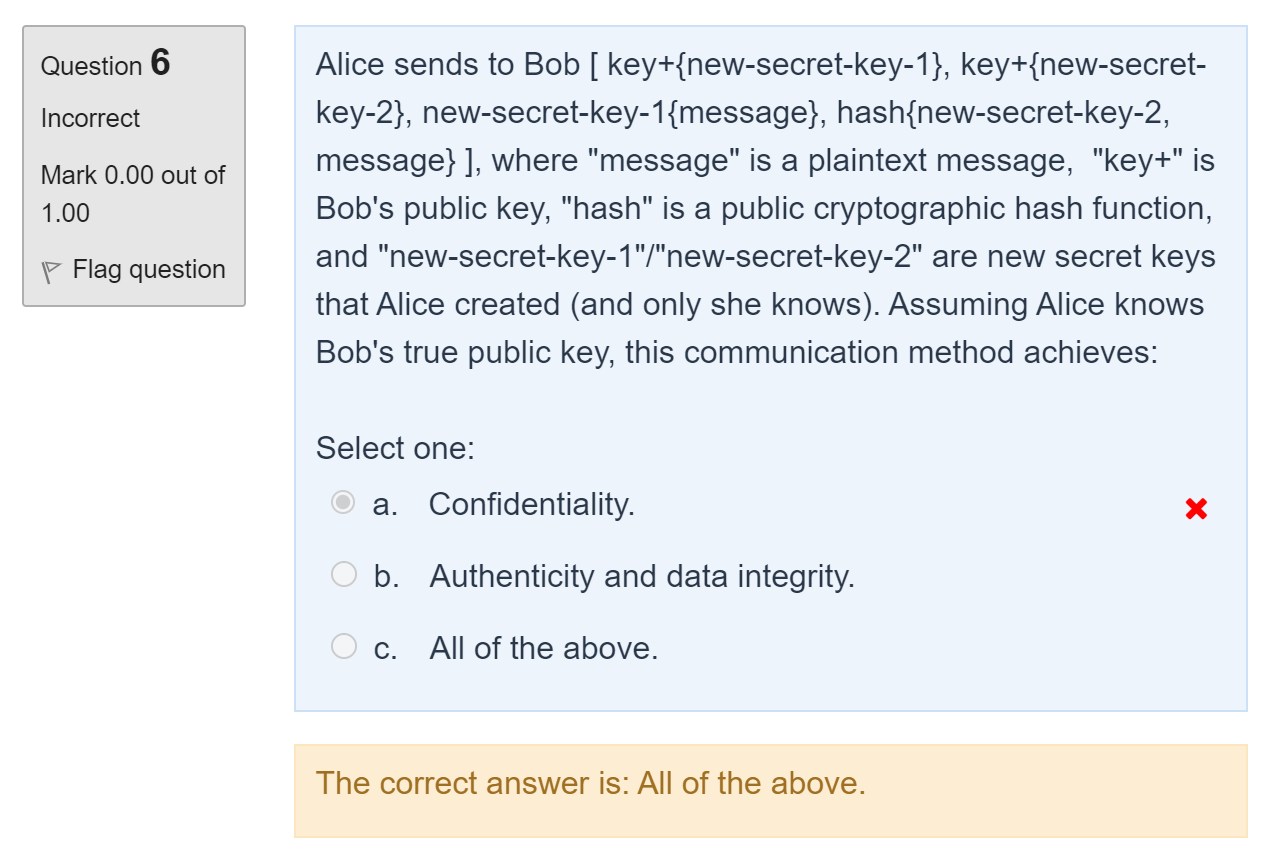
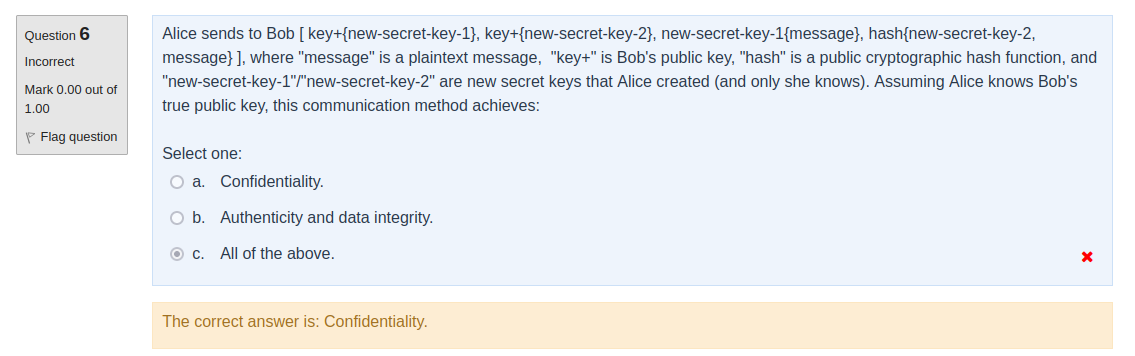
Hello,
For this question, I don't understand how it is possible that this communication method achieves authenticity.
In fact, if we have access to the communication channel between Alice and Bob, wouldn't it be possible to simply delete the packet and create a new one matching the protocol since all the keys used here are either freshly created or public? And in that case, Bob will not be able to know who is the actual sender of the packet
Thanks in advance