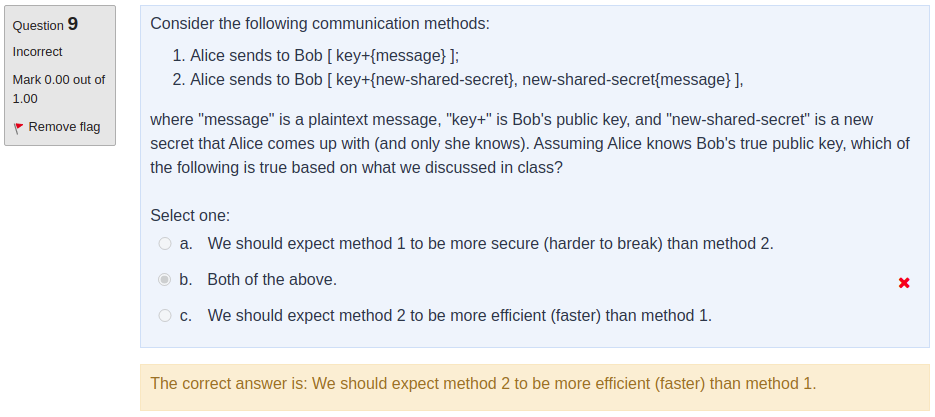
Hi,
I am reviewing the quiz and I don't understand what is wrong with my reasoning. (c.) is obviously true. Asymmetric encryption uses more computing power than the symmetric encryption.
But for (a.) I reason that it is harder to break. I do understand the basic that both asymmetric and symmetric encryption offers a compatible level of security if the key is only known by the authorized party.
However, Imagine if there is a vulnerabilities in Alice computer and we use the 2nd communication method. The malicious party gain access to the shared secret. Then, the malicious party would be able to read all the previous communication of Alice and Bob (if he recorded them) and subsequent communication (if Alice didn't realize and still using the same key.)
This wouldn't happen with the 1st communication method. Malicious party gain nothing from gaining access into Alice computer. There are no shared secret to decrypt anything.
In my conclusion, 1st communication method poses 1 point of failure (Bob PC) and 2nd communication method poses 2 point of failure in series (Alice PC or Bob PC). Thus, the 1st method is more secure than the 2nd method.